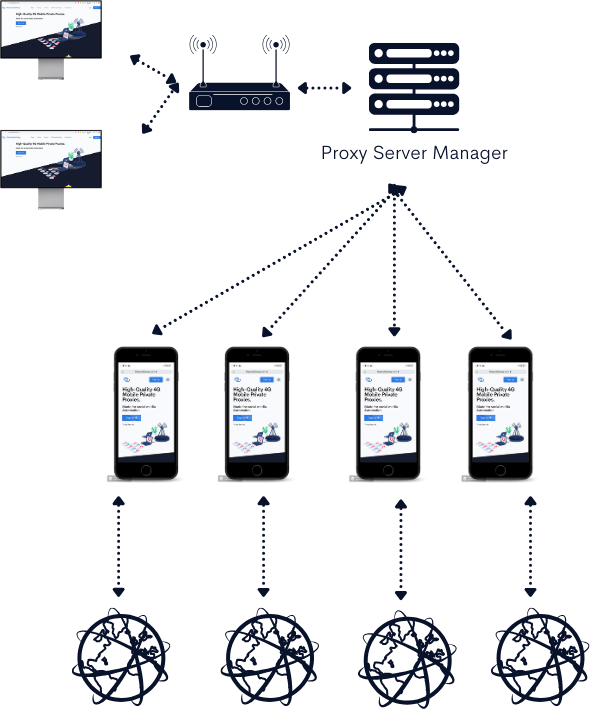
The Ethical Edge of Raw Mobile Proxies
Raw mobile proxies represent a paradigm shift in how proxy services operate. Unlike traditional methods, these proxies utilize real mobile phones or proprietary hardware to route traffic. This crucial difference lies in the ownership of the hardware or devices, which are fully owned by the company providing the proxy services. This direct ownership model ensures a transparent and ethical foundation, as there is no reliance on third-party devices without explicit consent.
This is where The Social Proxy distinguishes itself, by maintaining full ownership of all hardware and devices.
Why You Should Care
For anyone whose device is being used by a botnet/SDKs:
The implications of unwittingly being part of a proxy network extend beyond mere participation. These networks pose a security threat. Furthermore, this involuntary participation grants third parties access to your network, uses your bandwidth—which could incur costs or affect quotas—and could tie your IP address to unwanted activities,possibly complicating personal and professional situations.
For Proxy Users:
For those utilizing proxy services, it’s crucial to consider the ethical implications of your chosen provider. Aligning with services that exploit devices without explicit owner knowledge skirts ethical boundaries and abuses trust. It’s essential to question whether you want to support or not such practices.
Conclusion
The digital realm demands not only innovation but also ethical responsibility. Raw mobile proxies emerge as a beacon of ethical practice in the proxy service industry, offering a transparent, owner-consented approach to routing traffic. As we navigate the complexities of online anonymity and data scraping, choosing ethically sound proxies becomes paramount for both individual security and collective digital integrity.